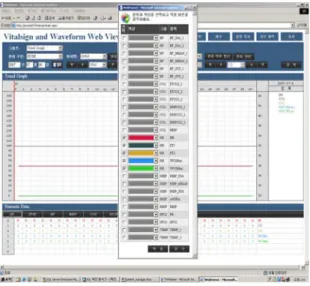
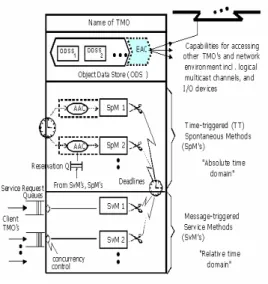
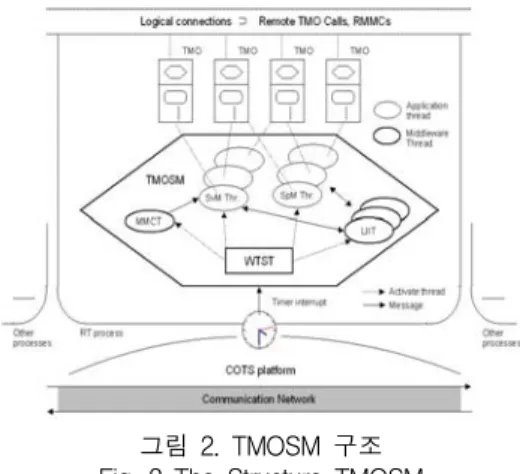
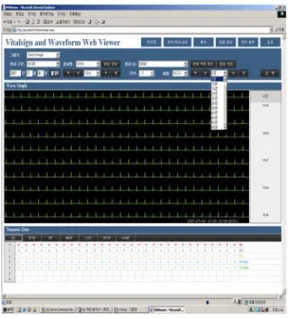
The Implementation of Vital Sign Information Parsing Module using TMO(Time Triggered and Message Triggered Method)
전체 글
수치

관련 문서
improvement(High Case Model) ···32 Figure 4.10 Comparison of before- and after-chemical treatment on cumulative gas production and Plateau time(High Case Model) ···34
"Two-phase pressure drop of refrigerants during flow boiling in small channels : an experimental investigation and correlation development",
2.1.15 "ITS" or "Intelligent Transport Systems" means the integration of information and communication technologies (ICTs) and applications that
De-assertion causes the NB or external clock generator to turn on the processor, and that takes place (a) in a sleep state: after a wake-up event is triggered; (b) in
Zhu, "Defending False Data Injection Attack on Smart Grid Network Using Adaptive CUSUM Test," Proceeding of the 45th Annual Conference on Information Sciences
"The Principle of Separating Economics from Politics, and Prospects for Improvement in North-South Relations." East Asian Review.. The Korean Journal
"Stress Heterogeneity in Teh Granite of the Soultz Egs Reservoir Inferred from Analysis of Wellbore Failure." In Proc World Geothermal Congress 2010, Paper
Based on the experimental results, the execution time in the matching process for 36 fingerprint minutiae, 200 chaff minutiae and 34 authentication fingerprint