ㆍ악성코드 감염방지 및 사용자 부정행위 방지를 위한 통합 관리 시스템 구현
전체 글
수치
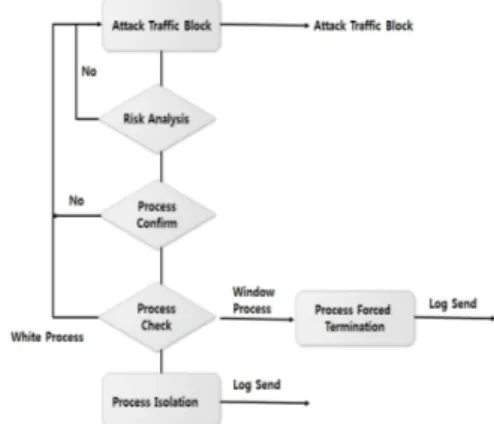
관련 문서
The change of Chinese government's policy, which has already changed the business environment to invest in China or the plans to enter China, is an important variable
Mean LV wall thickness (F) was higher when the ECM bi-layer patch was utilized. Pre-Ortho and Pre-ECM represent patch thickness prior to implantation.. Multi photon explants
For a successful ethical management, a nation should try to improve its business environments and both managers and employees are willing to keep the
By the HCI command on Bluetooth application program, the ACL packet types are changed and the link quality values are confirmed in several environments and
Crosswalk said goodbye to Grandma and the security guard and went off hurriedly.. After that, she often went
The “Asset Allocation” portfolio assumes the following weights: 25% in the S&P 500, 10% in the Russell 2000, 15% in the MSCI EAFE, 5% in the MSCI EME, 25% in the
Fig. Security Threats in Cloud Environments.. completely removed when the user leaves the existing cloud environment [4-12]. A user who has left creates a problem if he /
The captain deployed Russian military to Seoul not only to guard the Russian legation but also to escort King Gojong when he carried out the royal refuge to the Russian